In many enterprise organizations, the term "AI" can evoke immediate concerns about data privacy, security, and compliance. It's a reaction often born from uncertainty about how these powerful technologies handle sensitive information. However, the reality is that leveraging artificial intelligence doesn't inherently mean compromising your organization's integrity. Self-hosting your AI tooling, for instance, presents a robust solution that effectively balances potent capabilities with the stringent security controls that modern enterprises demand.
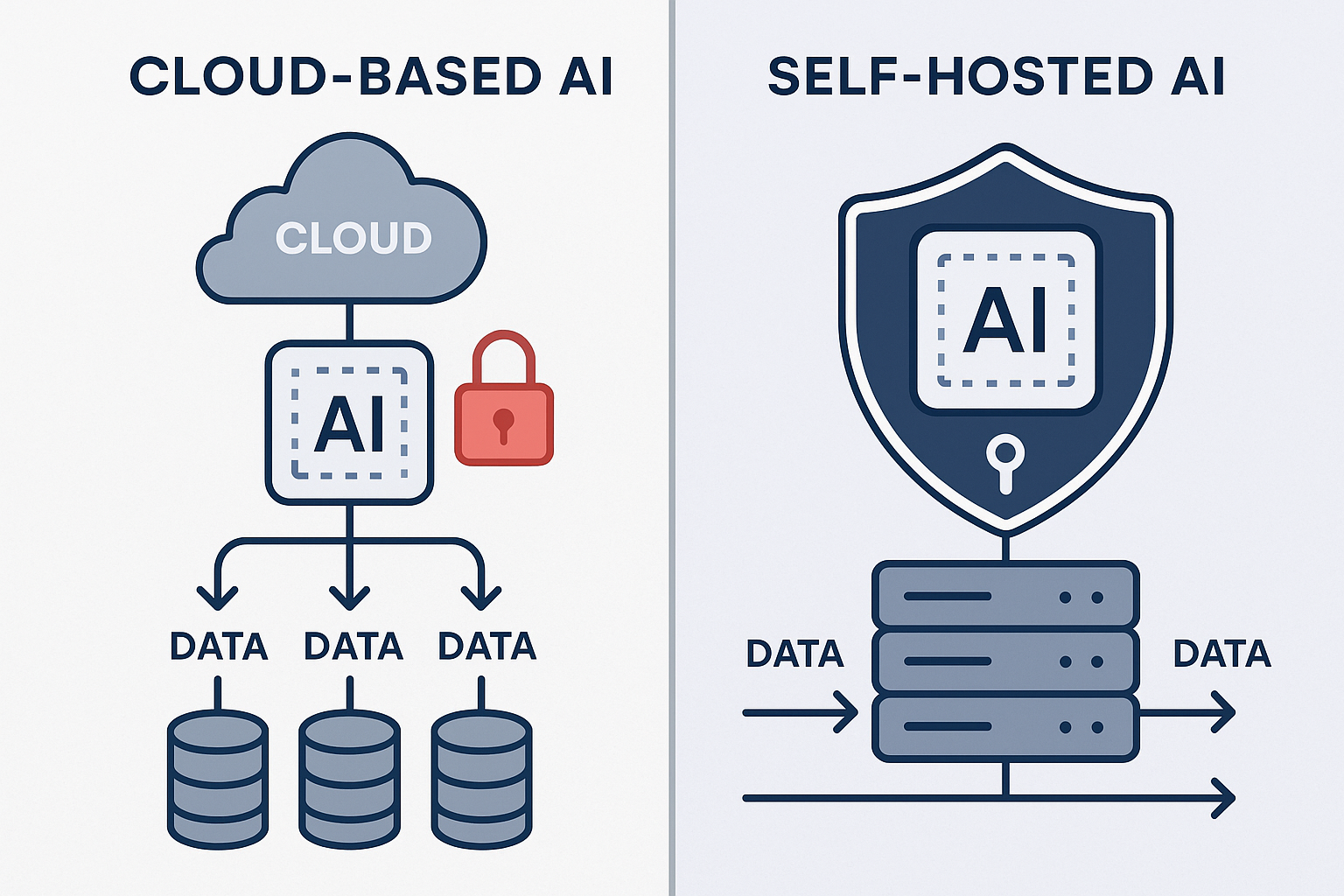
The Security Advantage of Self-Hosting
When you choose to self-host AI models, one of the most significant benefits is maintaining complete control over your data. Unlike many cloud-based AI services that require transmitting your information to external servers for processing, a self-hosted approach ensures your sensitive data never leaves your designated environment. This foundational control is paramount for organizations handling proprietary, confidential, or regulated information.
Furthermore, self-hosting allows for the meticulous implementation of your organization's specific security policies and compliance requirements. This means you can enforce your established data encryption standards, configure granular access control mechanisms, and maintain comprehensive audit logging capabilities. Network isolation controls can also be applied, further fortifying your AI instances against unauthorized access.
For organizations with the most stringent security postures, such as those in finance, healthcare, or government, self-hosted AI models can even be deployed in completely air-gapped environments. This setup, which has no external network access, effectively eliminates the risk of data exfiltration and provides the highest level of data assurance.

Powerful Capabilities Without Compromise
Opting for self-hosting doesn't mean you're sacrificing the power and knowledge that makes AI so transformative. Modern large language models (LLMs) are pre-trained on vast datasets of publicly available information. When you self-host these models, they bring this extensive knowledge base into your secure environment, often eliminating the need for the model to make external calls for general information, thus reducing your attack surface.
Crucially, a core principle of many self-hosted AI solutions is that your queries and data are not used for training the model. This is a critical distinction from some cloud AI services where user interactions can be absorbed into the model's learning corpus. With a self-hosted setup, your prompts, the data you process, and your specific usage patterns remain completely private and confidential to your organization.
Self-hosting also unlocks greater flexibility for customization. You can fine-tune models on your organization's domain-specific data, creating an AI that understands your unique jargon, processes, and context. Performance can be optimized for your specific hardware configurations, and you have the freedom to implement custom guardrails and ethical AI measures that align with your company's values and operational standards.
Implementation Considerations
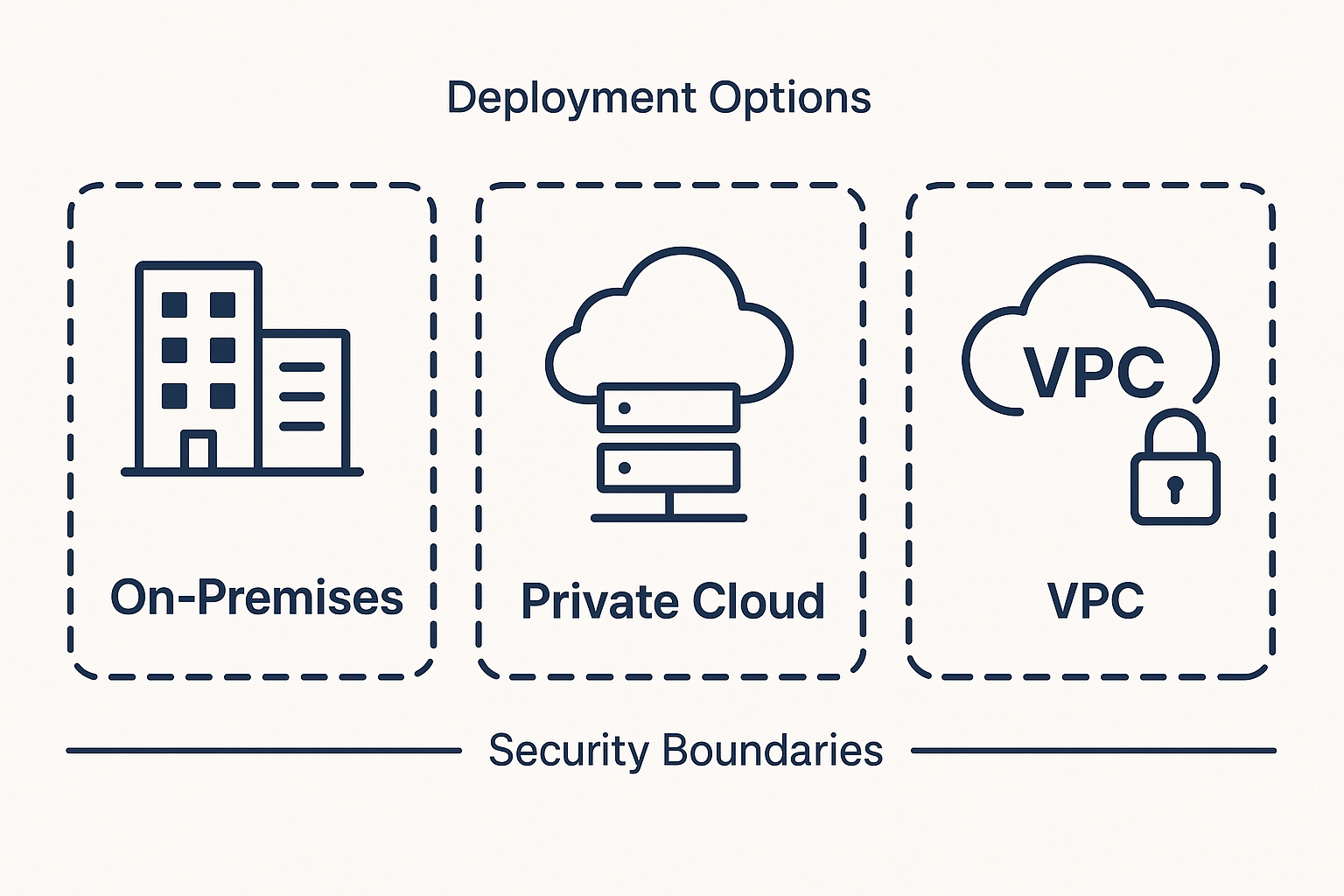
Deploying self-hosted AI can be approached in several ways, depending on your existing infrastructure and strategic preferences. You might choose an on-premises deployment within your own data center, leverage your private cloud environment on platforms like AWS, Azure, or GCP, or utilize a dedicated virtual private cloud (VPC) for an added layer of isolation.
Regarding resource requirements, it's important to note that AI models are becoming increasingly efficient. While some cutting-edge, full-scale models demand significant computational power, there's a growing spectrum of options. Organizations can deploy distilled models tailored for specific use cases or quantized models that are optimized for resource efficiency, allowing for effective AI implementation even with more constrained hardware resources.
How Adding Amy Supports Secure AI Implementation
At Adding Amy, we deeply understand the critical importance of security in AI deployments. It's not just an afterthought for us; it's a core component of our philosophy and product design. A significant majority of our enterprise customers choose self-hosted options, and through these partnerships, we've developed substantial expertise in guiding organizations through the process of implementing secure and effective AI solutions.
Our approach is collaborative. We work closely with your security and IT teams to thoroughly assess your specific requirements and threat model. Based on this understanding, we recommend appropriate deployment architectures and diligently implement security best practices. Our commitment extends beyond initial deployment, as we provide ongoing support and updates to ensure your AI environment remains secure and performs optimally.
Our clients consistently report that our guidance has been instrumental in helping them navigate the complexities of secure AI deployment. They've been able to harness the full power of AI to drive productivity and innovation while satisfying their most rigorous security and compliance mandates.
"Partnering with Adding Amy allowed us to implement a self-hosted AI solution that met all our stringent security requirements. We gained the productivity benefits we were seeking without compromising our data integrity. Their expertise was invaluable."
- CIO, Fortune 500 Financial Services Company
Self-hosting your AI tooling is not about choosing between capability and security—it's about achieving both. It empowers your organization to leverage the transformative potential of AI with the confidence that your data and operations remain protected. Contact us to learn how we can help your organization implement secure, powerful AI solutions tailored to your needs.